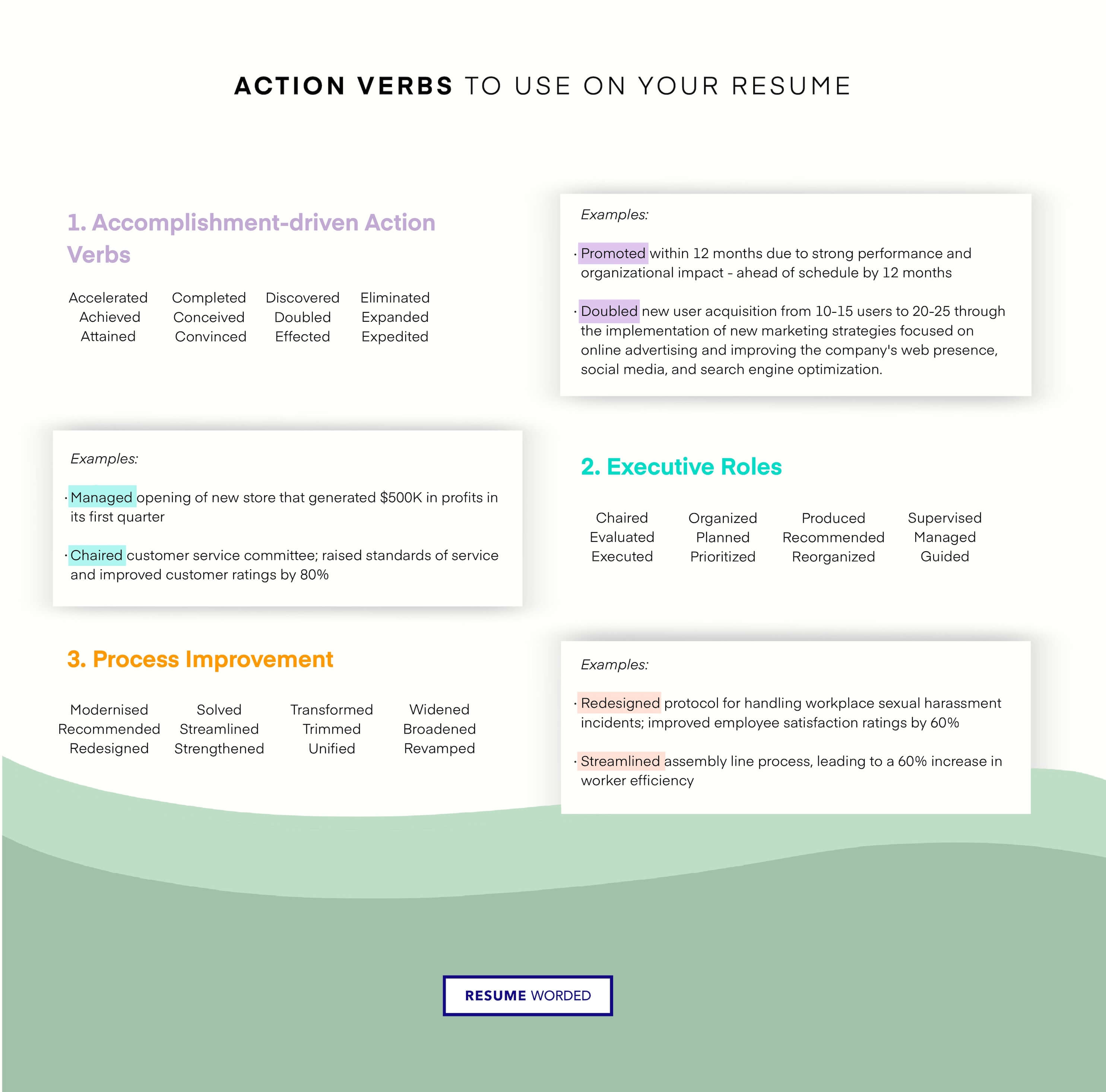
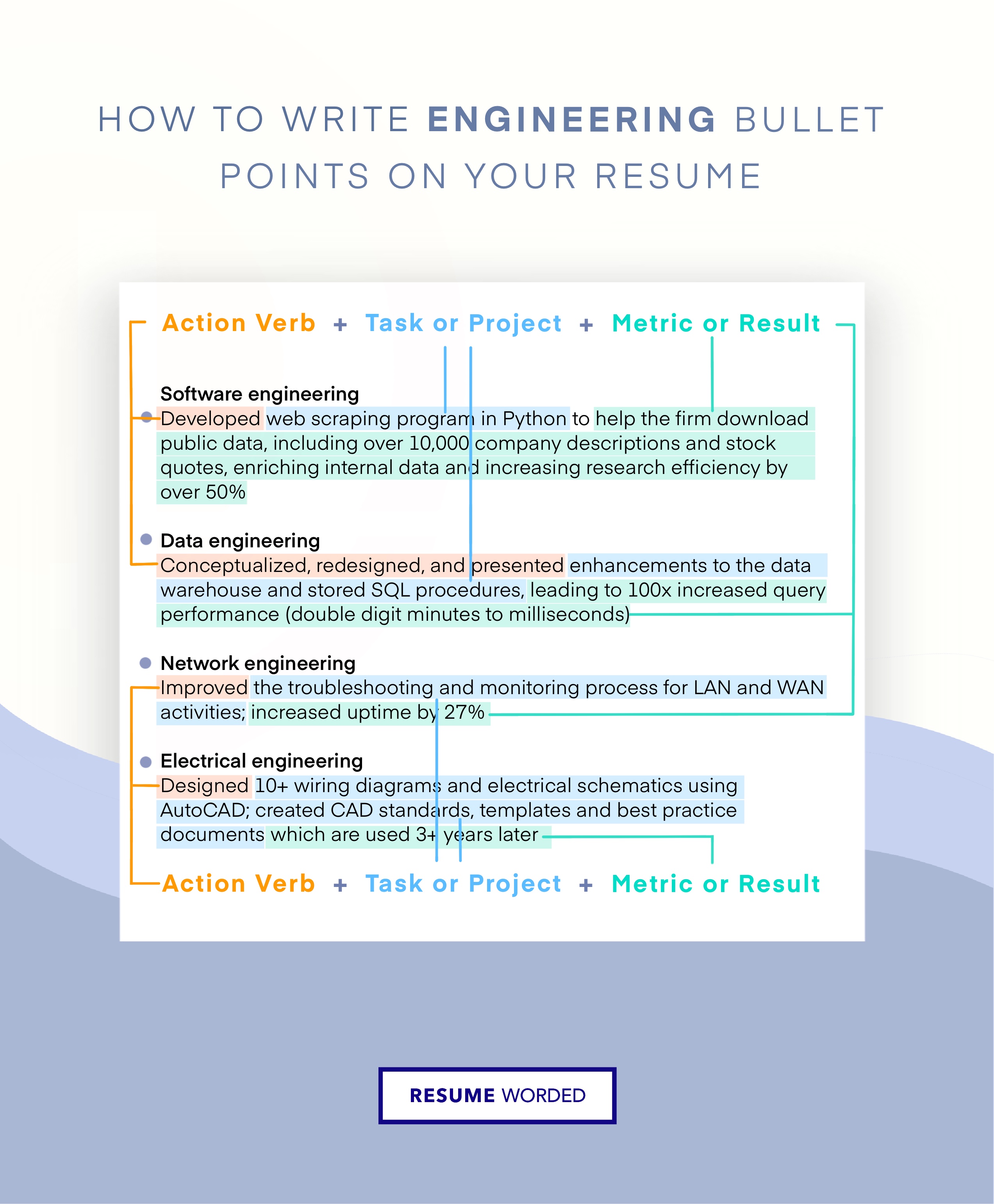
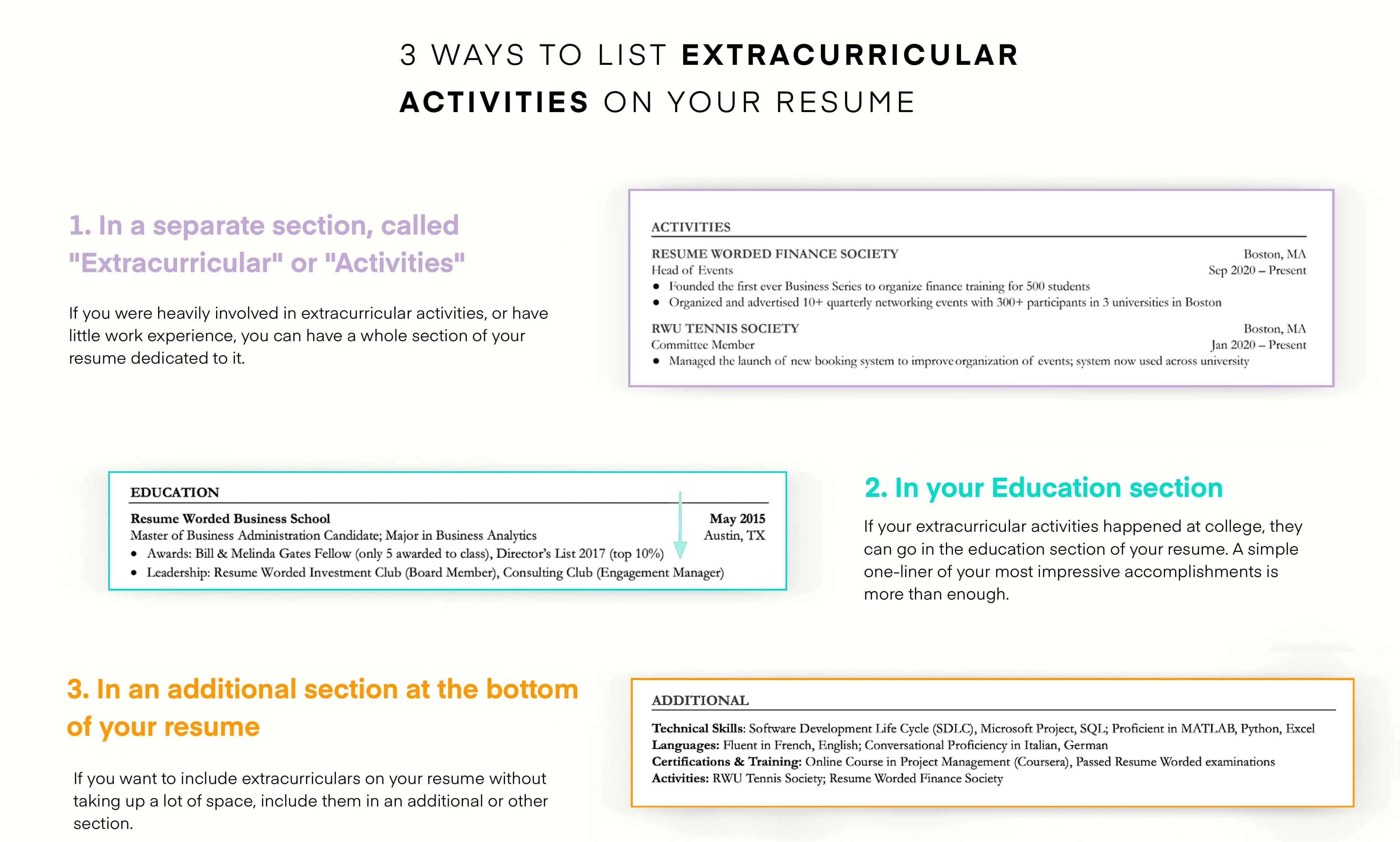
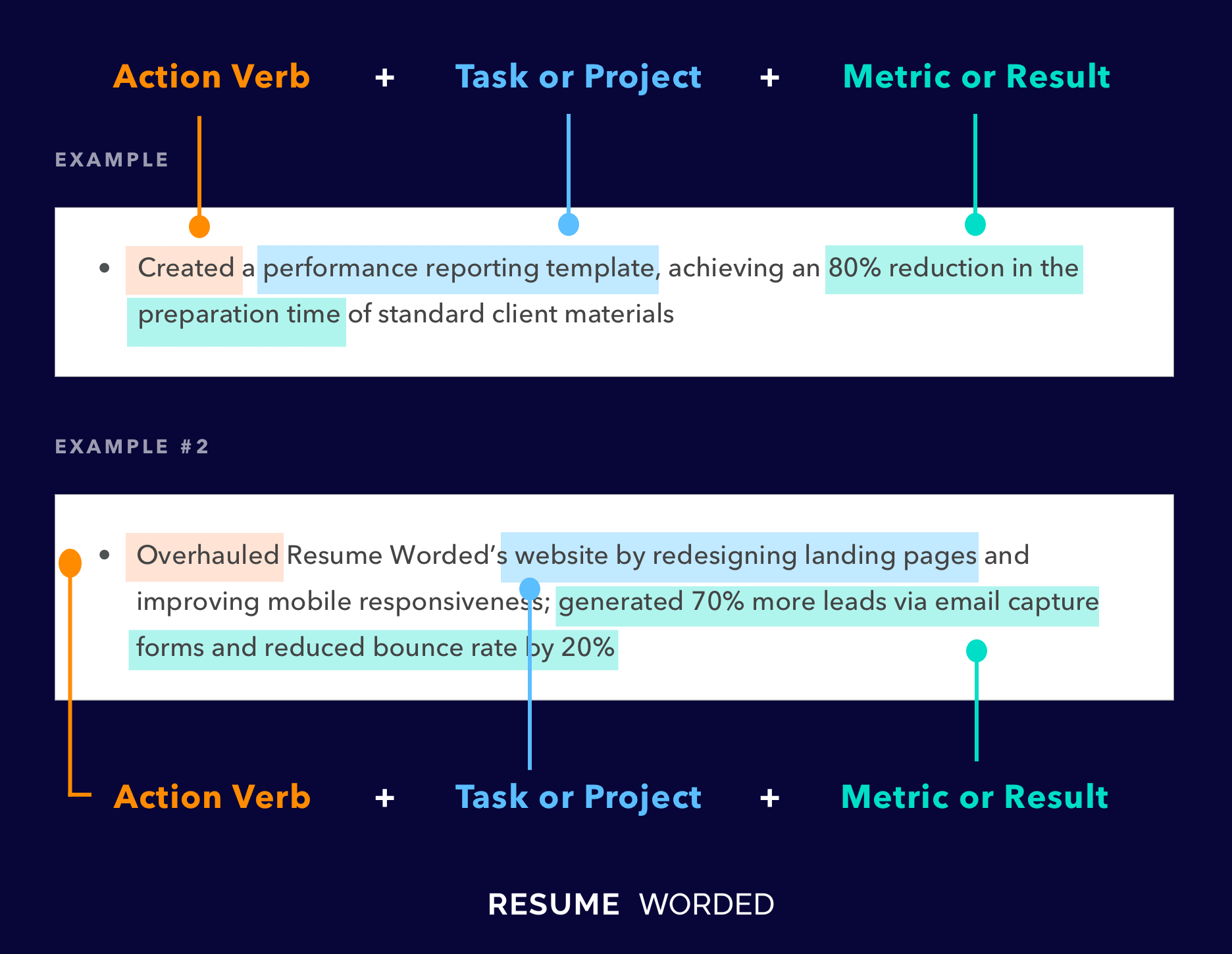
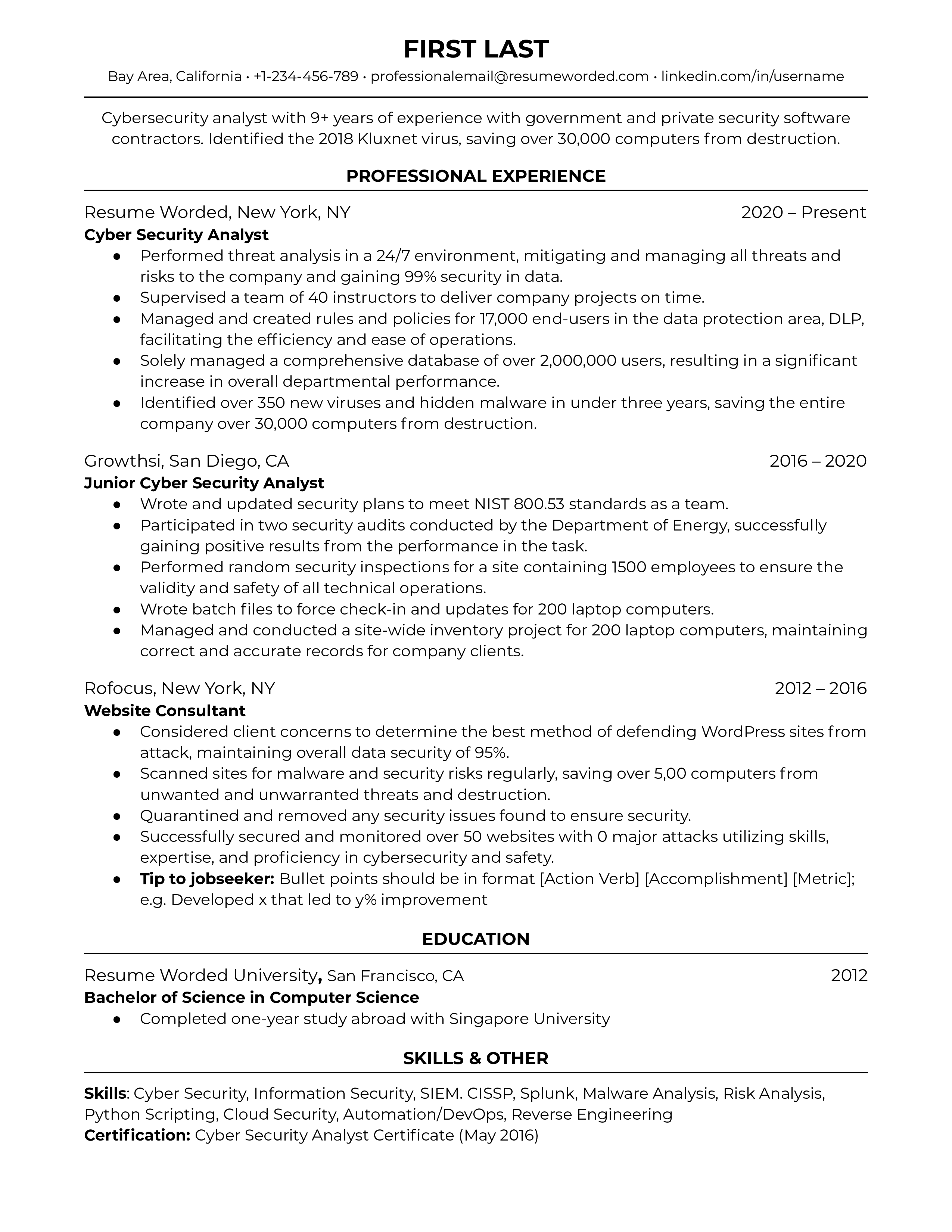
Detail past security project accomplishments
It’s important to demonstrate your competence throughout past positions in maintaining the integrity of computer systems and infrastructure. Like an IT Manager or IT Infrastructure Manager, this position is heavily project-oriented, so you should outline successful projects where you made an impact on the organization. Include aspects of the project such as scope and outcome, and be specific as you can with details.
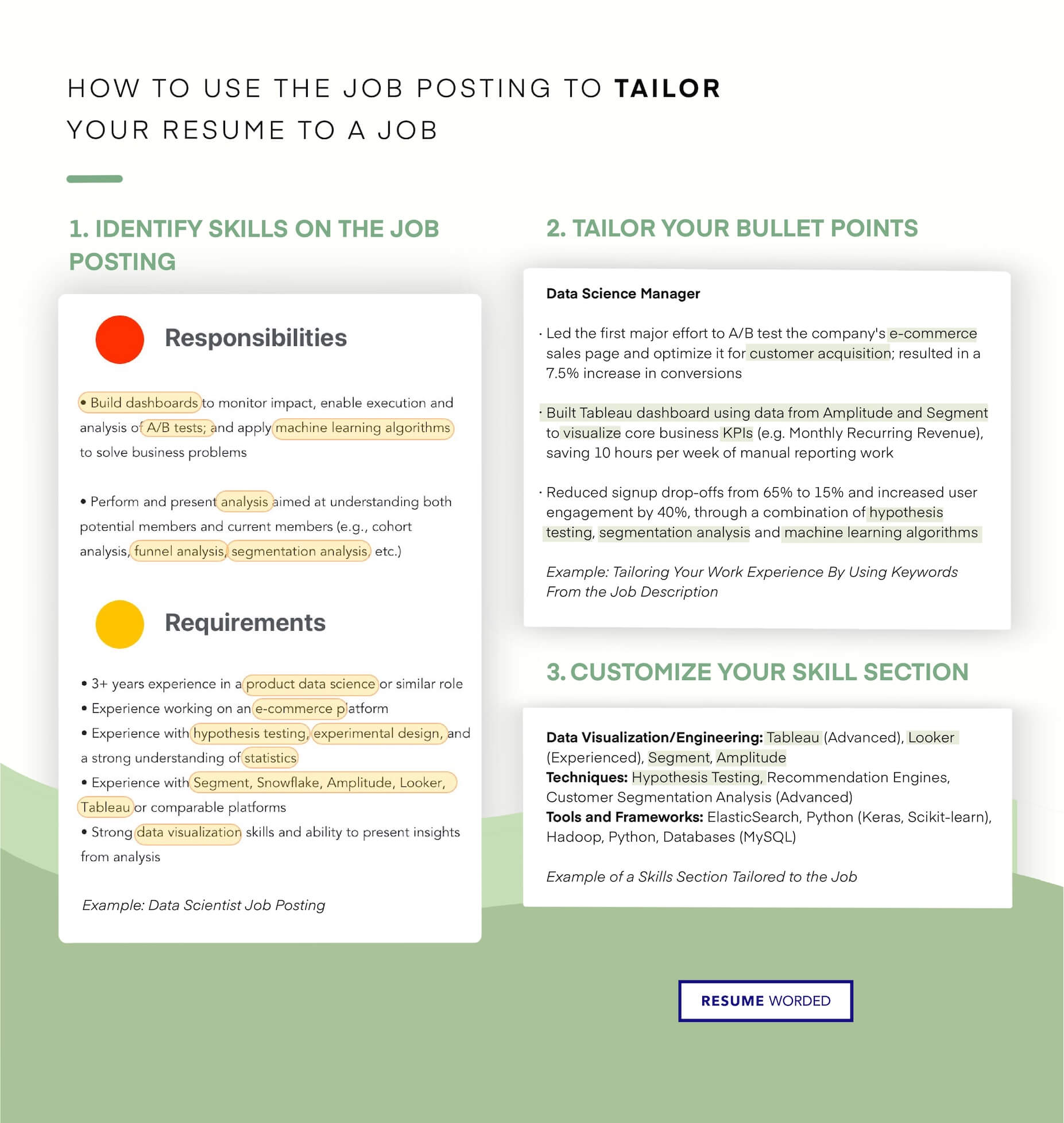



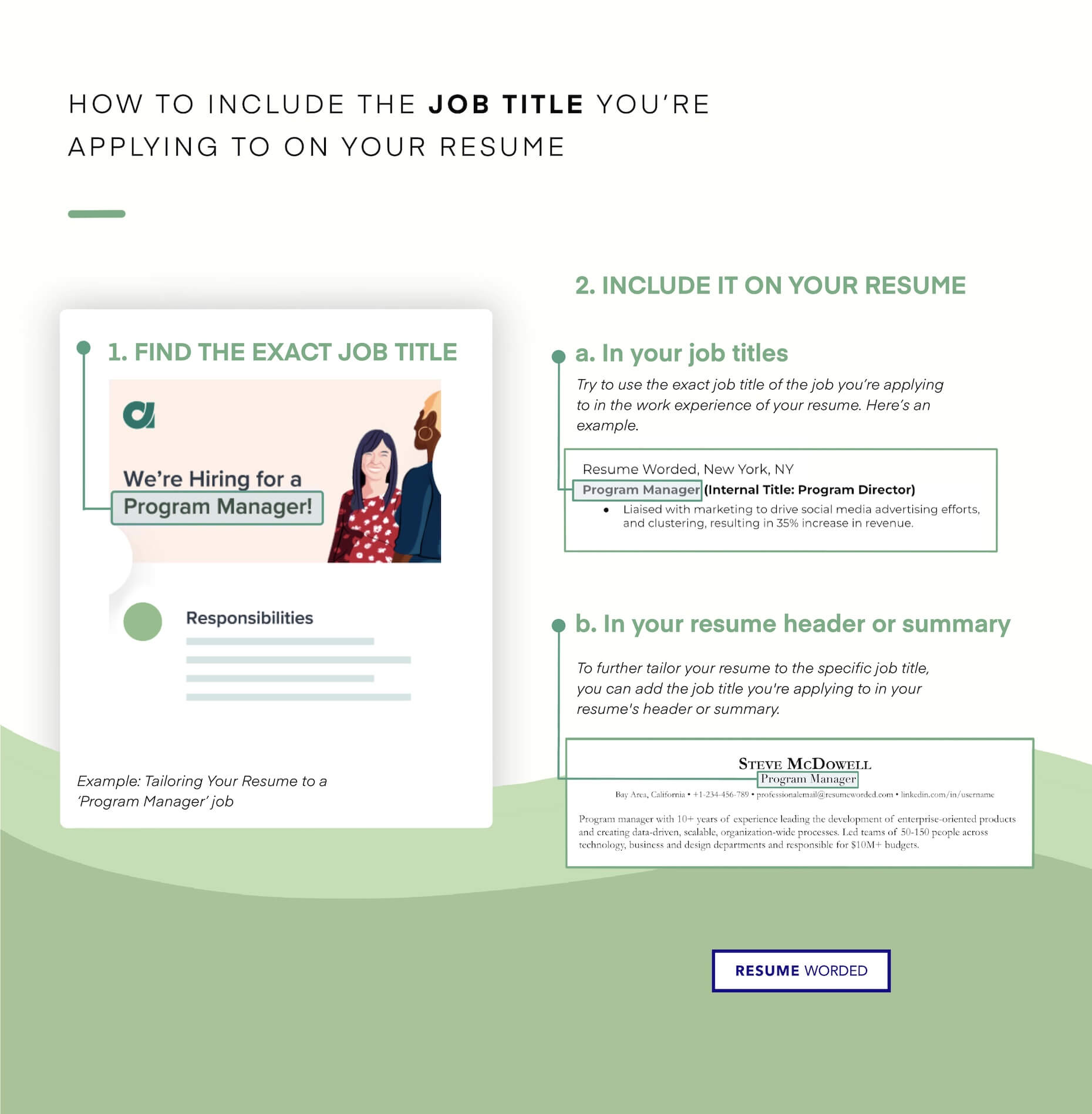





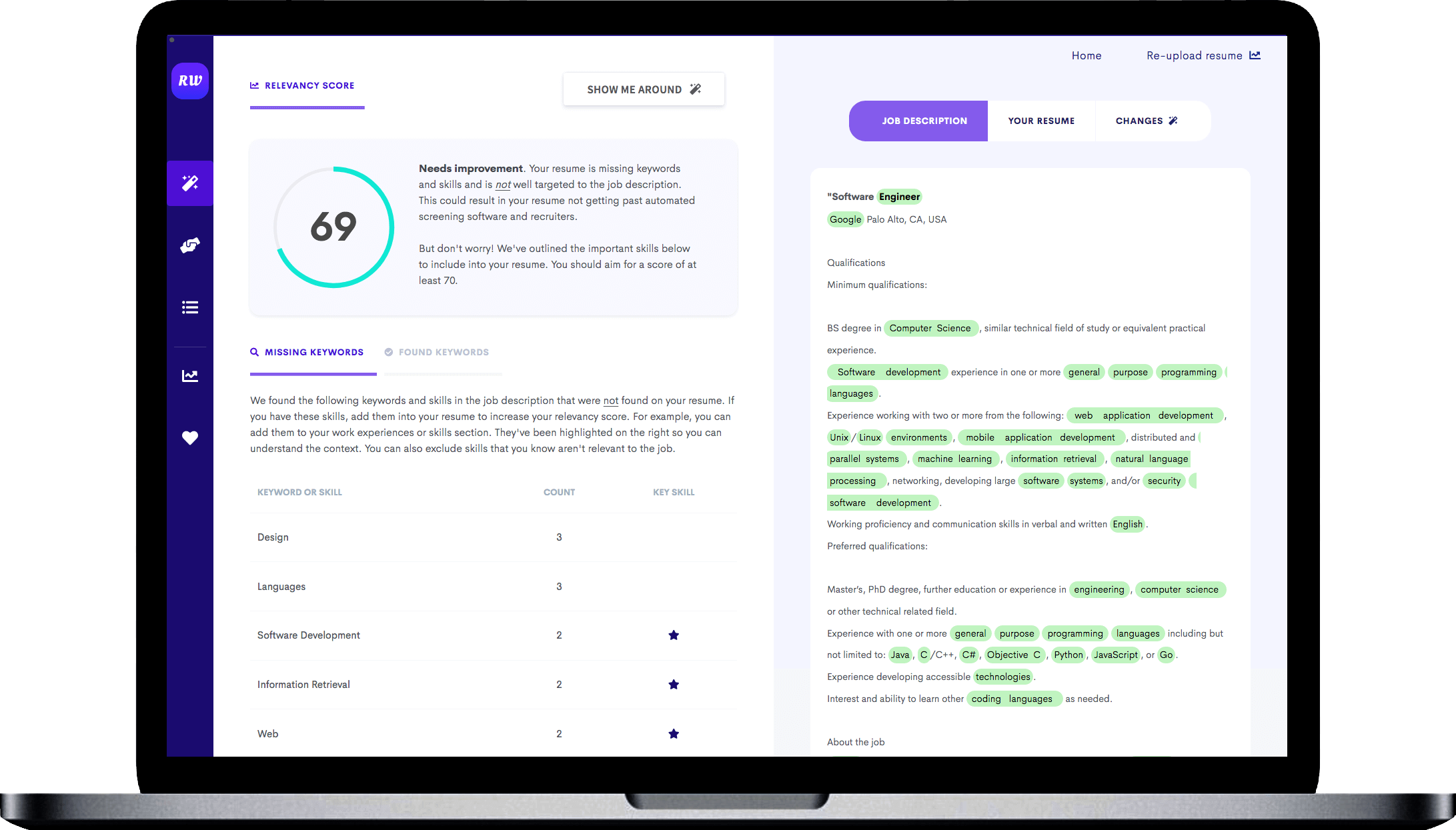
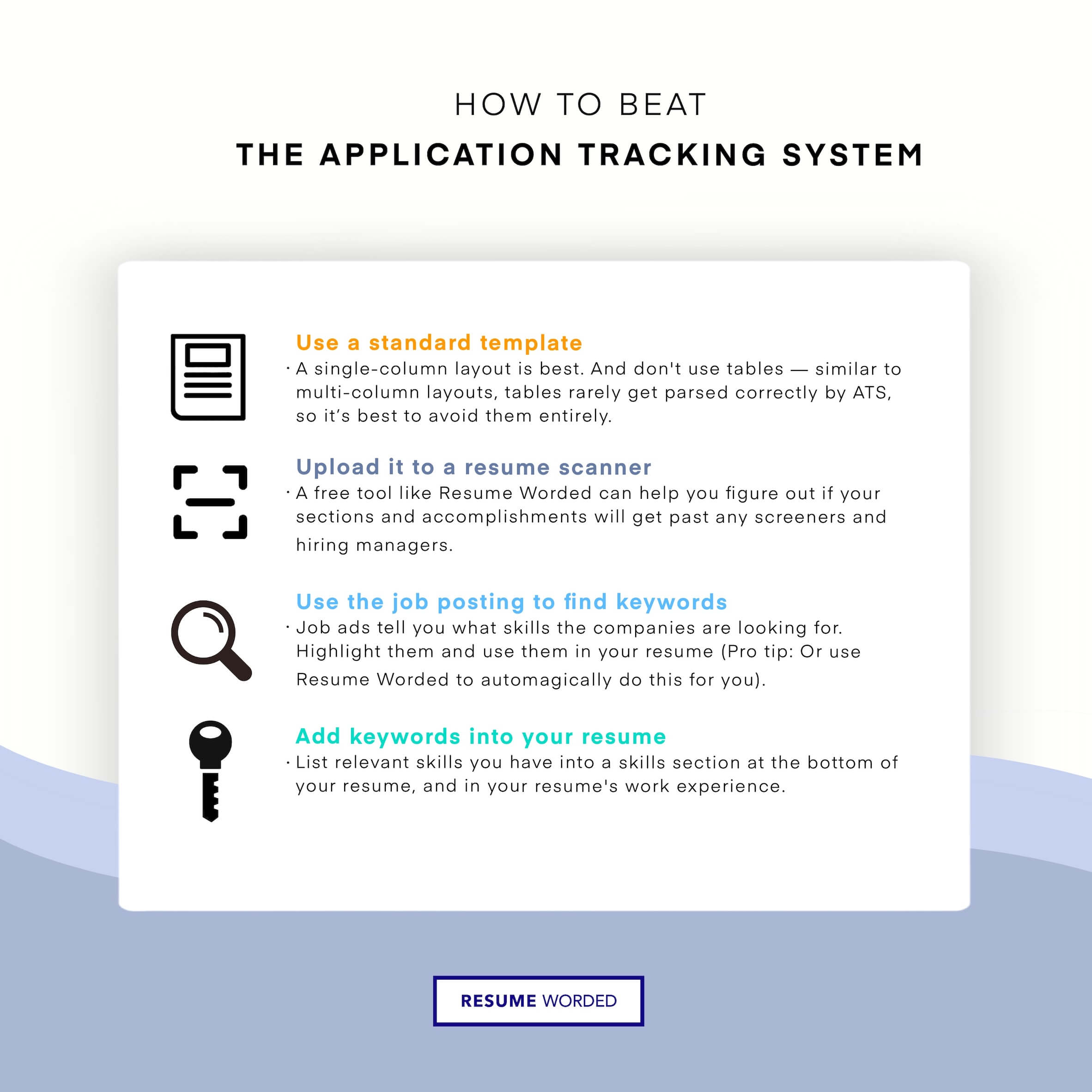 ATS (applicant tracking system) filters. - Cyber Security Engineer Resume"/>
ATS (applicant tracking system) filters. - Cyber Security Engineer Resume"/>