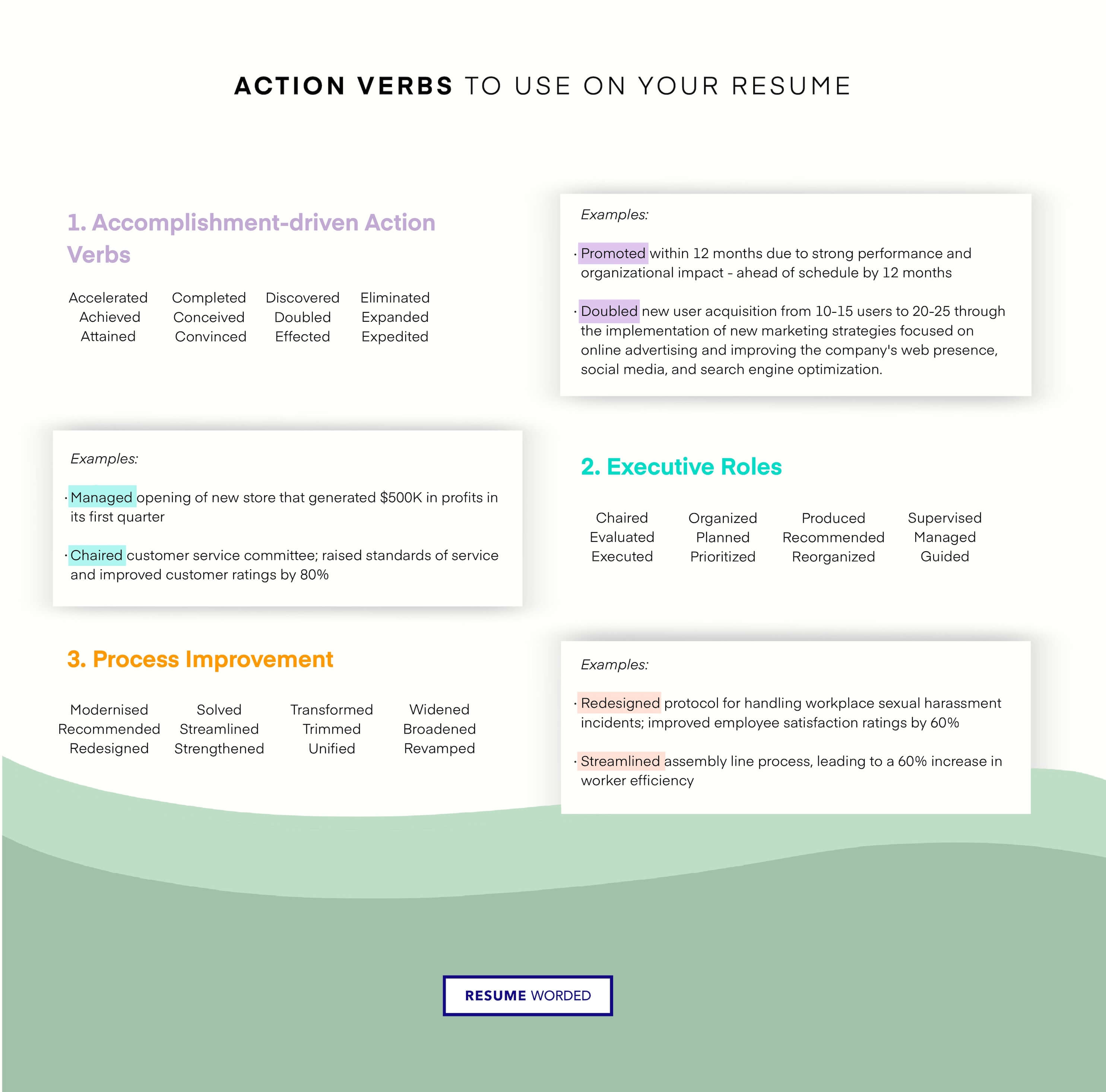
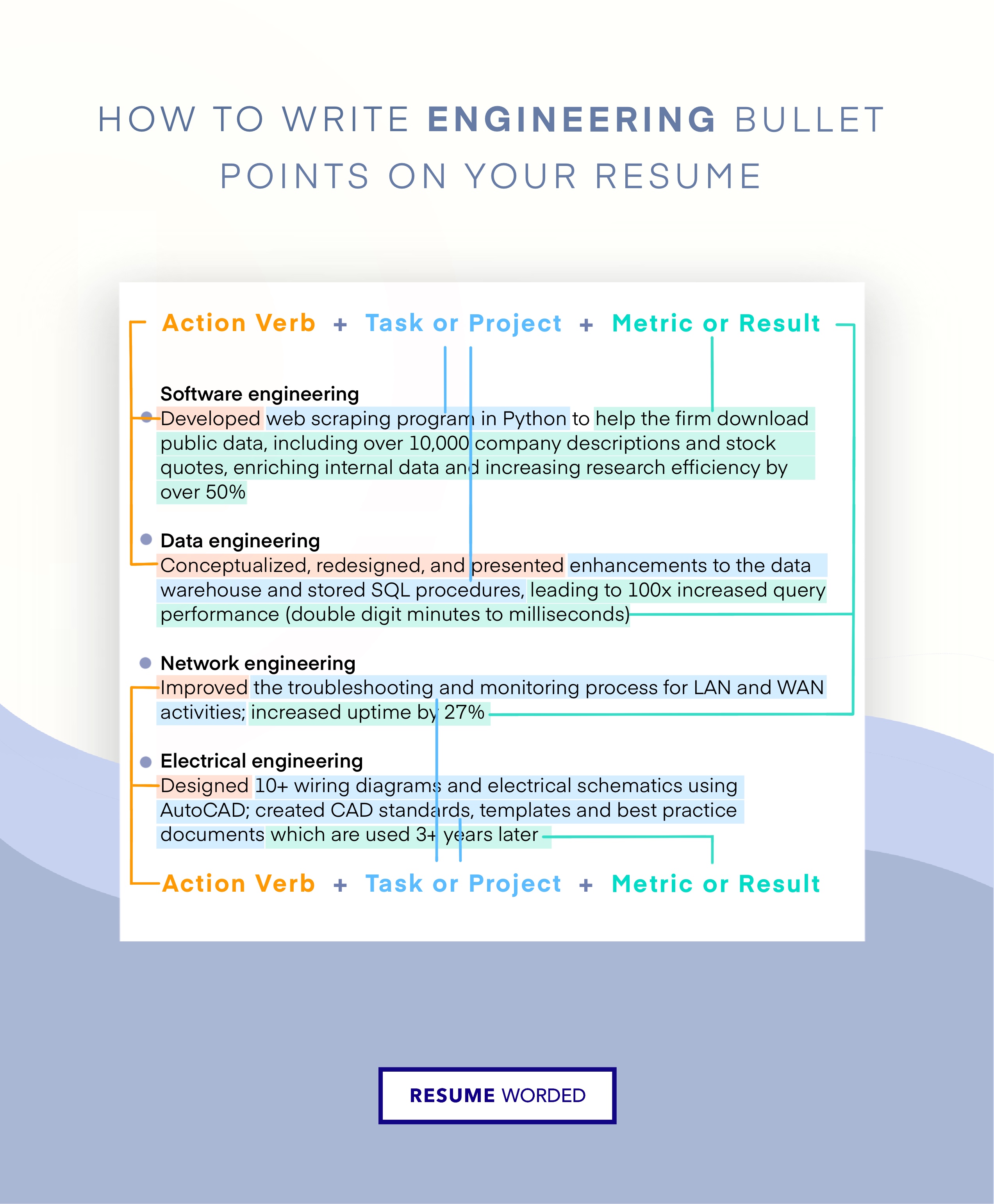
Demonstrate soft skills through bullet points
CIOs need technological know-how, but as you progress along the corporate ladder, the importance of specific technical skills becomes balanced by the need for soft skills like leadership. Instead of listing these as you would normal hard skills, use your bullet points to illustrate how you’ve put these skills to use in a corporate environment.
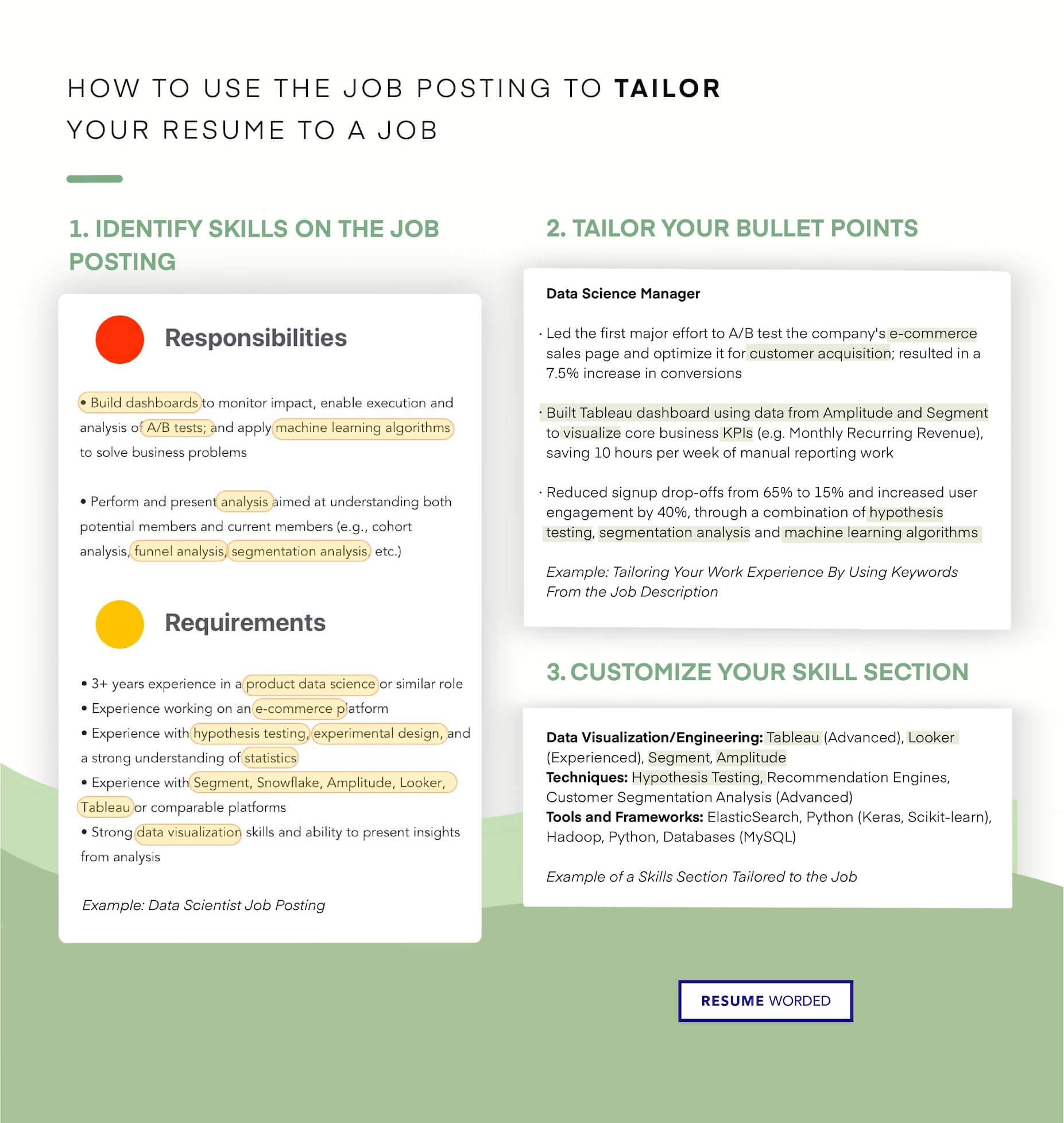









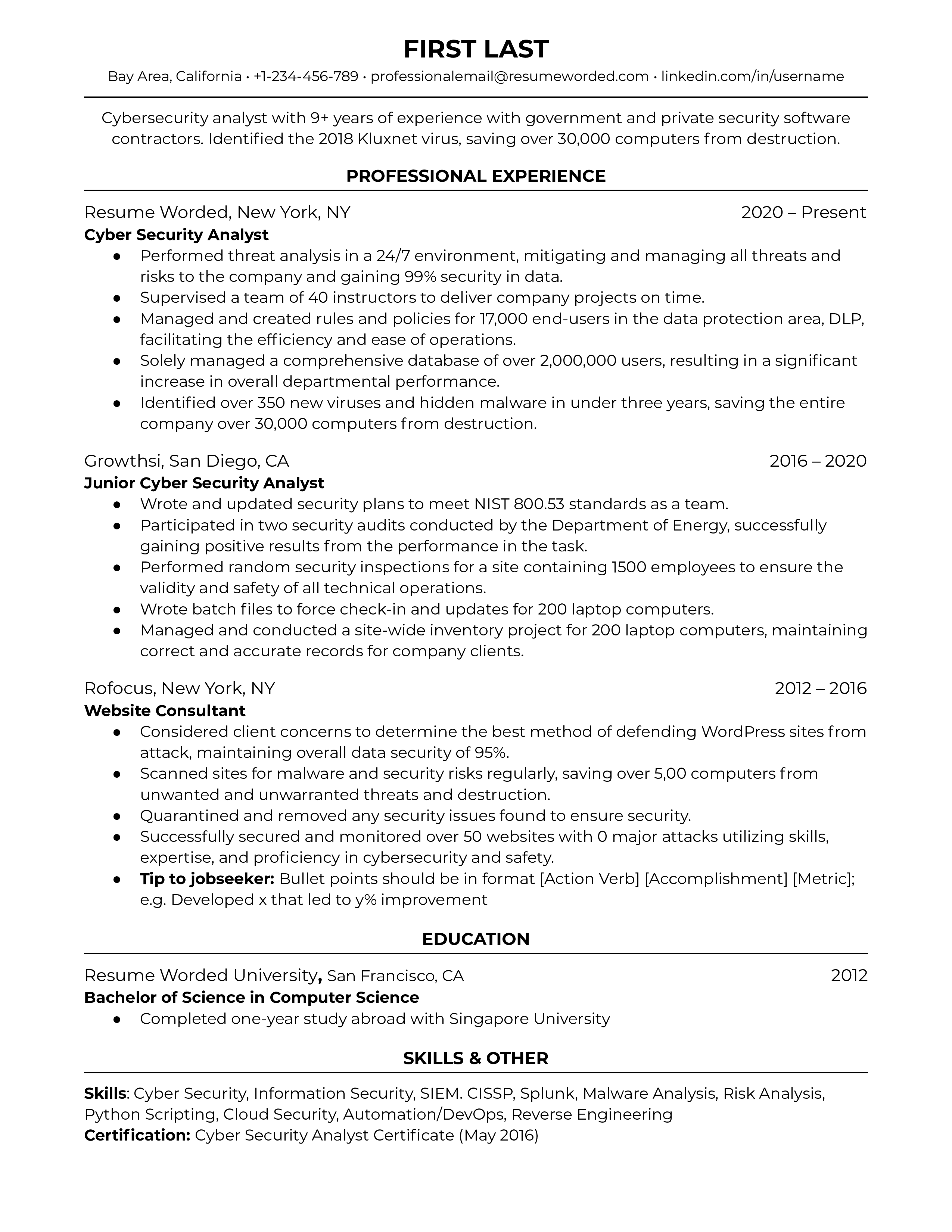
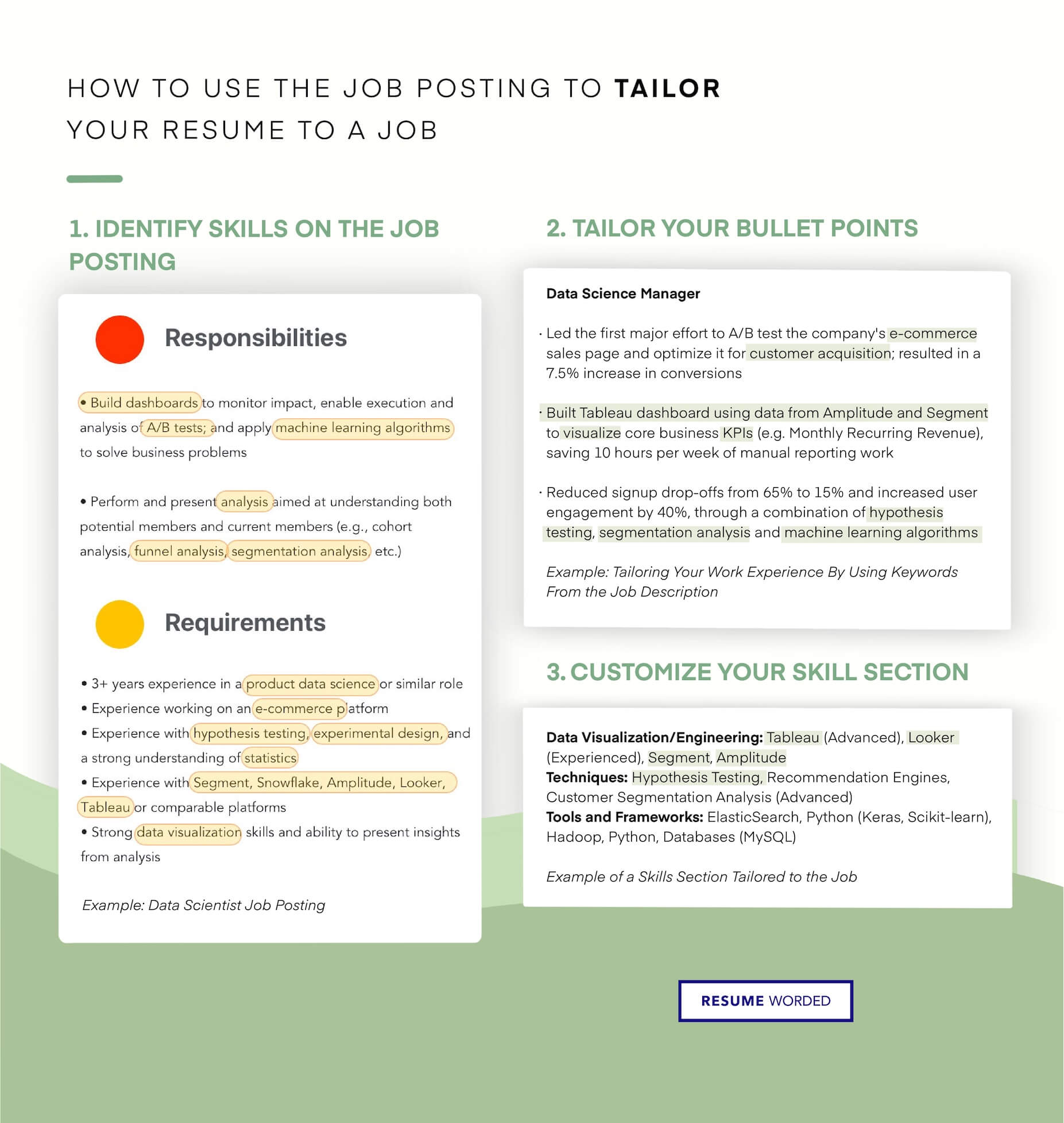



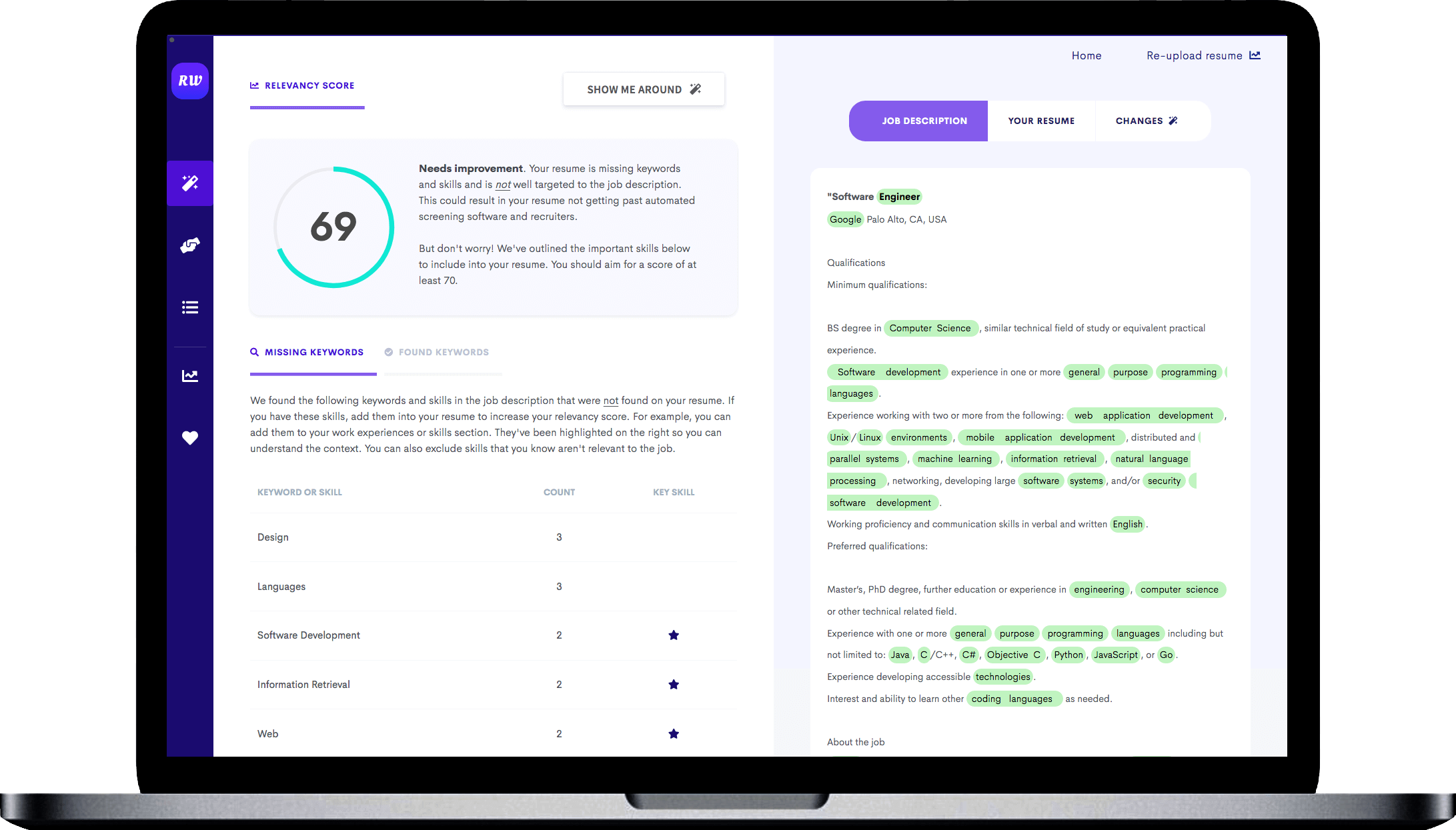
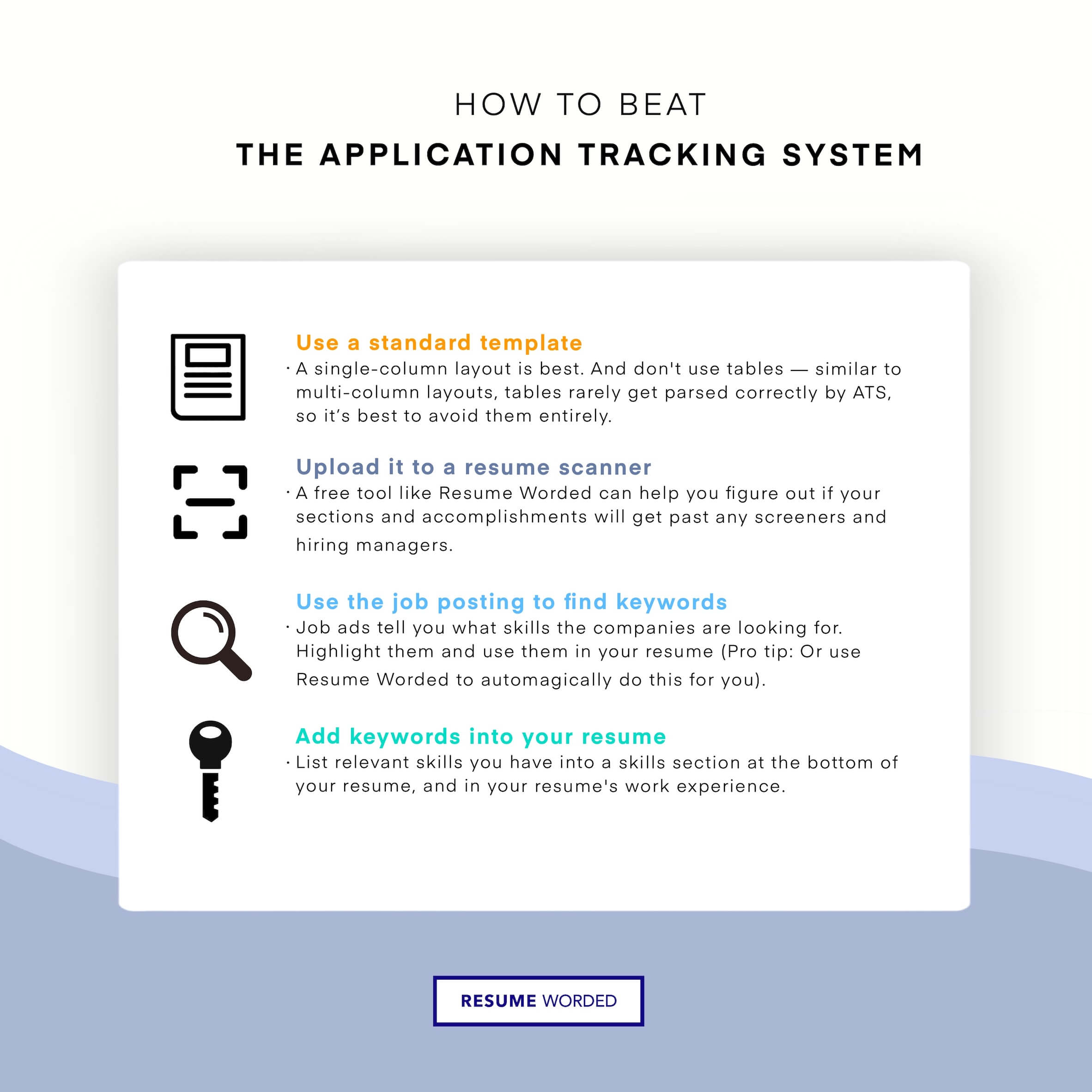 ATS (applicant tracking system) filters. - Cyber Security Engineer Resume"/>
ATS (applicant tracking system) filters. - Cyber Security Engineer Resume"/>